5. AppProxy Beta
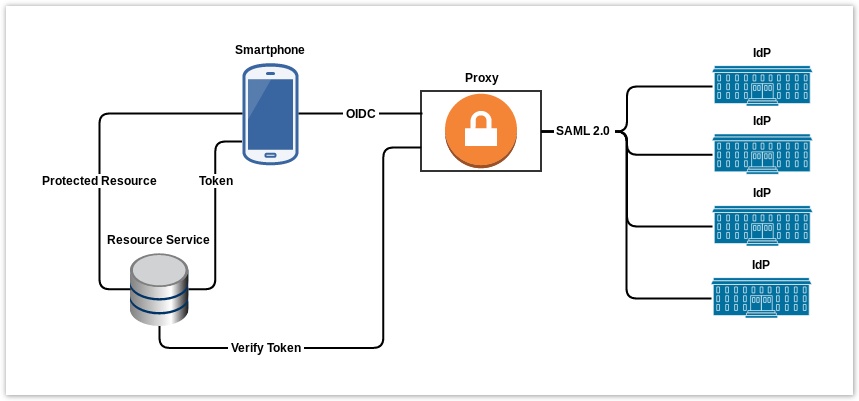
This proxy provides the ability to authenticate with a SAML identity federation through a mobile native application.
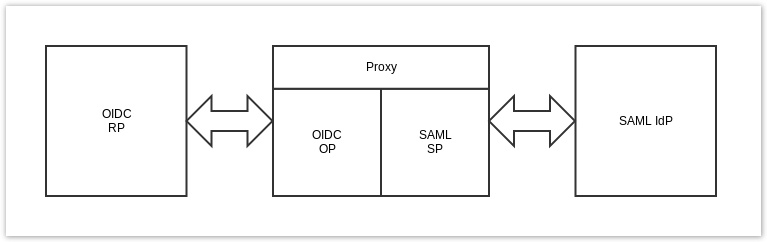
The proxy has an OpenID Connect frontend and a SAML2 backend. The frontend act as a OpenID Connect provider and accepts request from OpenID Connect Relying Parties. The backend act as a SAML2 Service Provider.
The Flow
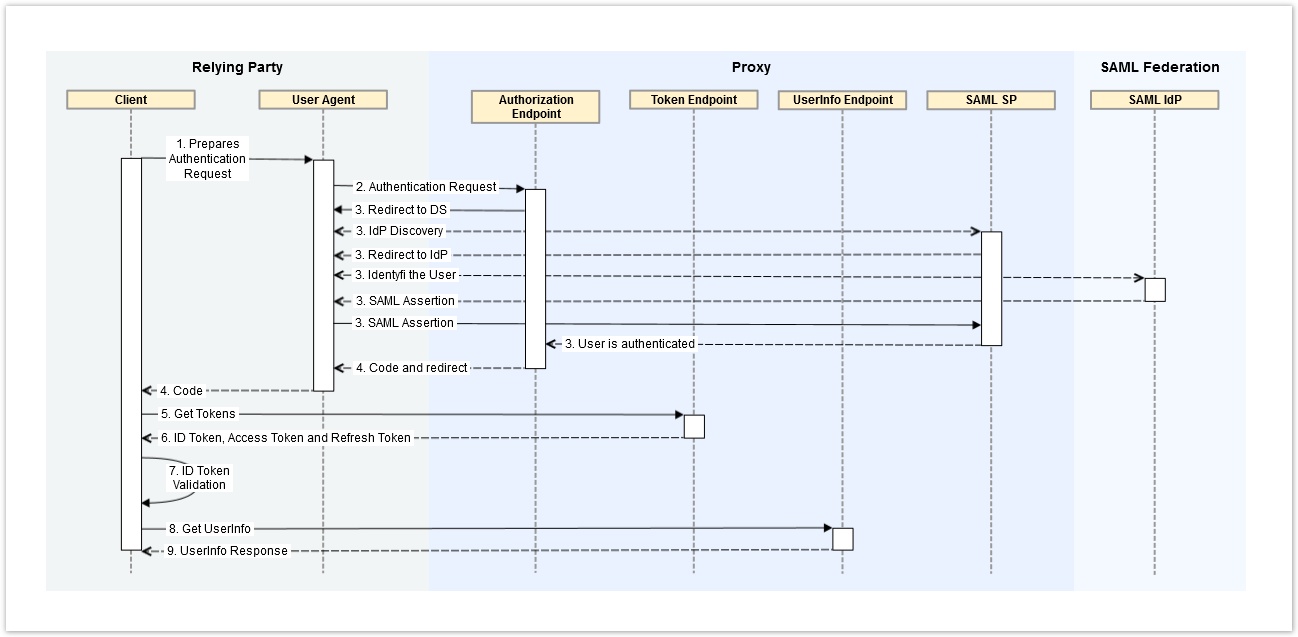
Authorization Code Flow
The OP Supports the Authorization Code Flow
- Client prepares an Authentication Request containing the desired request parameters.
- Client sends the request to the Authorization Server.
- Authorization Server Authenticates the End-User.
- Authorization Server sends the End-User back to the Client with an Authorization Code.
- Client requests a response using the Authorization Code at the Token Endpoint.
- Client receives a response that contains an ID Token and Access Token in the response body.
- Client validates the ID token and retrieves the End-User's Subject Identifier.
- Optional Client sends the UserInfo Request
- Optional Authorization Server sends the UserInfo Respons
Endpoints
Discovery
Get the endpoints and the capabilities of of the OP
GET https://apptest.skolfederation.se/.well-known/openid-configuration HTTP/1.1
Host: apptest.skolfederation.se
Authorization Endpoint
Example request that would be sent by the User Agent to the Authorization Server
GET https://apptest.skolfederation.se/Saml2/OIDC/authorization
?scope=openid
&response_type=code
&client_id=7ueo1swctdtc
&redirect_uri=se.skolfederation.7ueo1swctdtc%3A%2F%2Flocalhost
&state=b34ge6c2efe18do
&nonce=e62gr1vz7e46tl HTTP/1.1
Host: apptest.skolfederation.se
- scope The scope value must containe the
openidscop value and may include others. - response_type The Proxy supports the Authorization Code Flow. response_type must be set to code
- client_id The client identifier. There will only be manual registration. Conntact us and we will provide the client_id out-of -band
- redirect_uri Used for custom URI scheme redirects. We will provide the redirect_uri out-of -band
- state Random string value used to maintain state between the request and the callback to mitigate Cross-Site Request Forgery (CSRF, XSRF) attacks
- nonce Random String value used to associate a Client session with an ID Token and to mitigate replay attacks OpenID Connect Core section 2 ID Token
Token Endpoint
Example Token Request that would be sent by the Client to the Authorization Server
POST https://apptest.skolfederation.se/OIDC/token HTTP/1.1
Host: apptest.skolfederation.se
Content-Type: application/x-www-form-urlencoded
client_id=7ueo1swctdtc
&grant_type=authorization_code
&code=fglxlhtyfQwYbYS6WxSbIA
&redirect_uri=se.skolfederation.7ueo1swctdtc%3A%2F%2Flocalhost
- grant_type: Must be set to authorization_code
- code: The Authorization Code retrived from the Authorization Endpoint
- redirect_uri: The redirect_uri used in the initial Authentication Request
Example Refresh Request that would be sent by the Client to the Authorization Server
POST https://apptest.skolfederation.se/Saml2/OIDC/token HTTP/1.1
Host: apptest.skolfederation.se
Content-Type: application/x-www-form-urlencoded
client_id=7ueo1swctdtc
&grant_type=refresh_token
&refresh_token=96f5d26d9aa74175b
&scope=openid
- grant_type: Must be set to refresh_token
- code: The Authorization Code retrived from the Authorization Endpoint
- redirect_uri: The redirect_uri used in the initial Authentication Request
UserInfo Endpoint
Example of a UserInfo Request that would be sent by the Client to the Authorization Server
GET https://apptest.skolfederation.se/OIDC/userinfo HTTP/1.1
Host: apptest.skolfederation.se
Authorization: Bearer 2fde563078f04f2
Authorization: The Access Token MUST be sent as a Bearer Token
Introspection Endpoint
Example of a Introspection Request that would be sent by the Resource Service to the Authorization Server. The Resource Service must be registered as a Client whit the gran_type set to client_credential.
POST https://apptest.skolfederation.se/OIDC/introspection HTTP/1.1
Host: apptest.skolfederation.se
Accept: application/json
Content-Type: application/x-www-form-urlencoded
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW
token=2fde563078f04f2&token_type_hint=access_token
- token: The string value of the token
- token_type_hint: OPTIONAL. A hint about the type of the token submitted for introspection
JWKS URI
Fetch the public RSA key that are used to validate the ID Token.
GET https://apptest.skolfederation.se/OIDC/jwks HTTP/1.1
Host: apptest.skolfederation.se
Use appropriate library to download the JWK Set and validate the ID Token.
ID Token
The following optional Claim are used within the ID Token returned by the Proxy.
at_hash
Openid Connect Core section 3 ID Token